News
Web hackers’ den Yakadaya hosted and facilitated attackers
 Just hours after police launched an investigation into two cyber-attacks on President Maithripala Sirisena’s official website, an online forum called Yakadaya went down. It remained inaccessible at the time of going to press.
Just hours after police launched an investigation into two cyber-attacks on President Maithripala Sirisena’s official website, an online forum called Yakadaya went down. It remained inaccessible at the time of going to press.
Yakadaya was an identified meeting point for Sri Lanka’s hacker community. The Criminal Investigation Department (CID) notified court earlier this week that the two suspects arrested in connection with hacking of the presidential website had been interacting with each other through Yakadaya. Police also said the elder of the pair, a 27-year-old from Moratuwa, had been the forum’s administrator.
The attacks took place consecutively on August 25-26. Media attention focused on the younger suspect, a 17-year-old who allegedly posted a Sinhala language message on the website, beseeching the President, among other things, to reconsider a recent decision to shift the GCE A/Level examination from August to April. Ironically, he also advised the Government to be more mindful of the security of Sri Lanka’s websites to avoid a cyber-war.
The teenager is said to have learned hacking techniques and interacted with other hackers on Yakadaya. The forum was particularly popular because it was in Sinhala, said sources who knew of its activities. It had articles supported by graphics and video tutorials. It also facilitated group discussions.
Yakadaya’s page on the Facebook social network remains active. It contains links to articles published on the website that now cannot be accessed. A significant number of them are on hacking and website vulnerabilities, and are all in Sinhala.
The presidential website had been on WordPress, a freely-available Content Management System (CMS) known for its security issues. An article posted on Yakadaya, as recently as July 1, is titled ‘Wordpress Hacking’ and comes with a video tutorial. Another instructs users how to surf the internet while masking their Internet Protocol (IP) address. An IP is a unique numerical label assigned to each device that is part of a computer network.
The Sunday Times chose to withhold the teenager’s name as he is a minor. On his Facebook page, which we went through, he calls himself a student and a web designer. He had even started a fledgling website design business earlier this year. He seems a typical teenager with an interest in computers.
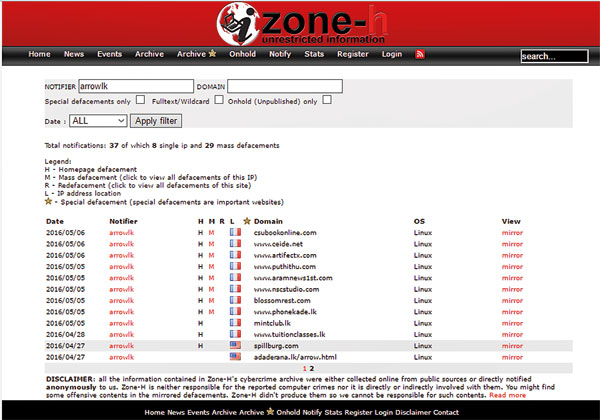
But the CID claimed to court that he could have an online persona, that of a hacker with the screen name ‘ArrowLK’ who was active on Yakadaya. The CID would not confirm to us whether ArrowLK was the teenager acting on his own or, if the account had been handled by several people.
ArrowLK’s Facebook page is now deactivated but, the Sunday Times accessed it while it was online. The last public post on its timeline indicates an interest in hacking accounts on the popular social networking service Instagram.
Zone-H is a web service that tracks web defacements and keeps an archive of cyber crimes. It records that ArrowLK defaced 37 Sri Lankan websites starting April this year. But ArrowLK has not claimed credit for defacing President Sirisena’s website. And this is where it gets murkier.
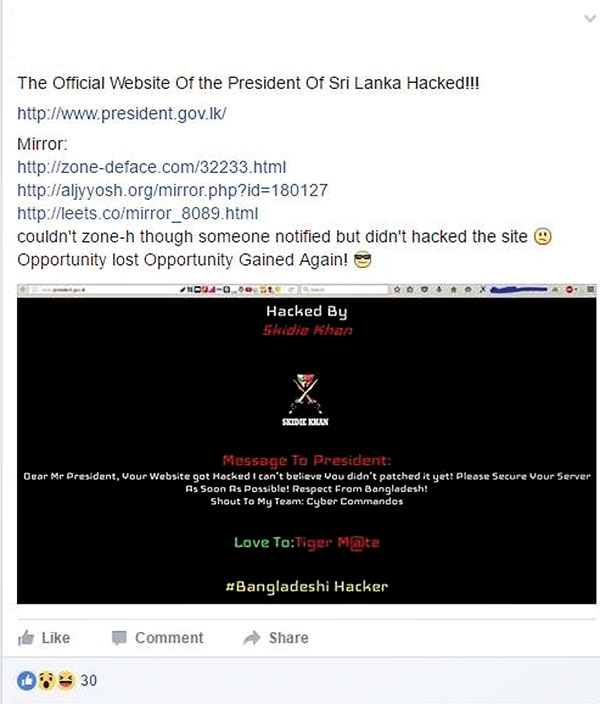
‘The Sri Lankan Youth’ have taken credit for the first attack on August 25. But a Bangladeshi hacker with the screen name ‘Skidie Khan’ claimed responsibility for the second one, the very next day. Investigators have identified two IP addresses linked to the hacking. One is located abroad, raising suspicions that hackers based overseas are working with those in Sri Lanka.
The hackers seem proud of their operation. The Sunday Times saw a screenshot of a Facebook post allegedly by Skidie Khan, bragging about the cyber attack. Only this time, he had posted it under his real name and tagged several others, including ArrowLK. This post has now been removed and the accounts deactivated.
Those familiar with this hacking culture derisively describe amateur local hackers as ‘script kiddies’. It refers to people who use tools or computer programs developed by others to attack computer networks or, deface websites in order to gain fame.
Osanda Malith Jayathissa is an independent security researcher and reverse engineer. He calls himself a ‘white hat’ or, “a person who hacks into a computer network in order to test or evaluate its security systems”. He believes the Bangladeshi hackers had developed a ‘backdoor shell’–a malicious piece of source code or computer instructions that can be uploaded to a site to gain access to files stored therein. This allowed their Sri Lankan counterparts to enter and deface the site.
The security precautions of many local websites, especially Government-run, were woefully inadequate, Mr Jayathissa warned. The onus was on website administrators to update themselves about such vulnerabilities and take adequate precautions.
“A simple Google search will lead you to all manner of articles on web vulnerabilities, how to exploit them and what you need to do to protect your site,” he said. “All this is publicly available information.”
Last year, the Sri Lanka Computer Emergency Readiness Team (SLCERT) received 20 complaints related to website defacement, both Government and private. This is down from a record high of 56 in 2014. That spike may be attributed to a mass cyber-attack named #OpSriLanka that started in April of that year. Teams of hackers from multiple countries had launched a coordinated assault on as many as 129 Government and corporate websites in Sri Lanka.
In 2013, there were 16 complaints. Cyber-attacks were in the news that year as well, when 22 Government sites belonging to the North-Central Provincial Council were targeted by a group calling themselves the ‘Bangladesh Grey Hat Hackers’. However, not all incidents are reported. Administrators are often happy to restore the sites and implement added security.
The attack on the President’s website does not seem to have resulted in the theft of valuable data or personal information. The hackers were chasing notoriety. It is also unlikely that the site held any privileged information that a hacker could sell to interested parties. This may not be the case with every site.
“When you have electronic information, there is very often some way of getting at that information,” explained Gihan Dias, Professor at the Department of Computer Science and Engineering, University of Moratuwa. “You must use all known methods to make them as secure as possible.”
Increasingly, Government and private organisations are going online in Sri Lanka, but computer security skills are not keeping apace. There are more opportunities for people to launch attacks, Prof. Dias said. There has been a steady increase in cyber-attacks over the past few years.
Not all hackers are troublemakers interested in defacing websites or stealing data, pointed out Mr Jayathissa. There are others–like him–who are ethical hackers or computer security experts that infiltrate computer systems to identify security flaws. They then alert network administrators about these holes. This is known as ‘responsible disclosure.’
Mr Jayathissa has been doing this awhile. He has detected potential security issues in the systems of several international organizations, including Facebook and Apple, which have publicly acknowledged his assistance.
“I have been telling youngsters online not to be misled and explaining they can use their skills for good,” he said. “Unfortunately, many want to follow in the footsteps of those who gain notoriety by doing all the bad things.”
| Hackers’ Gallery There are various types of hackers, said Sujit Christy, an information systems security professional. Script kiddy: Still learning hacking and motivated by a shallow desire to flaunt their newly-acquired skills amongst peers and to gain popularity by attacking networks and defacing websites. Hacktivist: They are usually motivated by politics, religion, exposing wrongdoing, exacting revenge or harassing their target. They sometimes acquire valuable information that they monetize. The Black Hat Hackers: They break into computers, networks or create computer malware to find the path of least resistance. They are methodical, disciplined and leverage advanced malware, spam, phishing and other cyber attacks with strategic intent and goals. State-sponsored hackers: Some Governments position themselves online to achieve military objectives. These hackers have unlimited time and funds to target civilians, corporations and Governments. Spy hackers: Hired hackers that infiltrate computers and networks of competing corporate sector organizations to steal trade secrets. Their primary objective is to serve a client’s goal and get paid. Cyber terrorist: Generally motivated by religious or political beliefs. They attempt to create fear and chaos by disrupting critical infrastructure. They are dangerous, with a wide range of skills and goals. |

